A2: Analog Malicious Hardware
Reference1
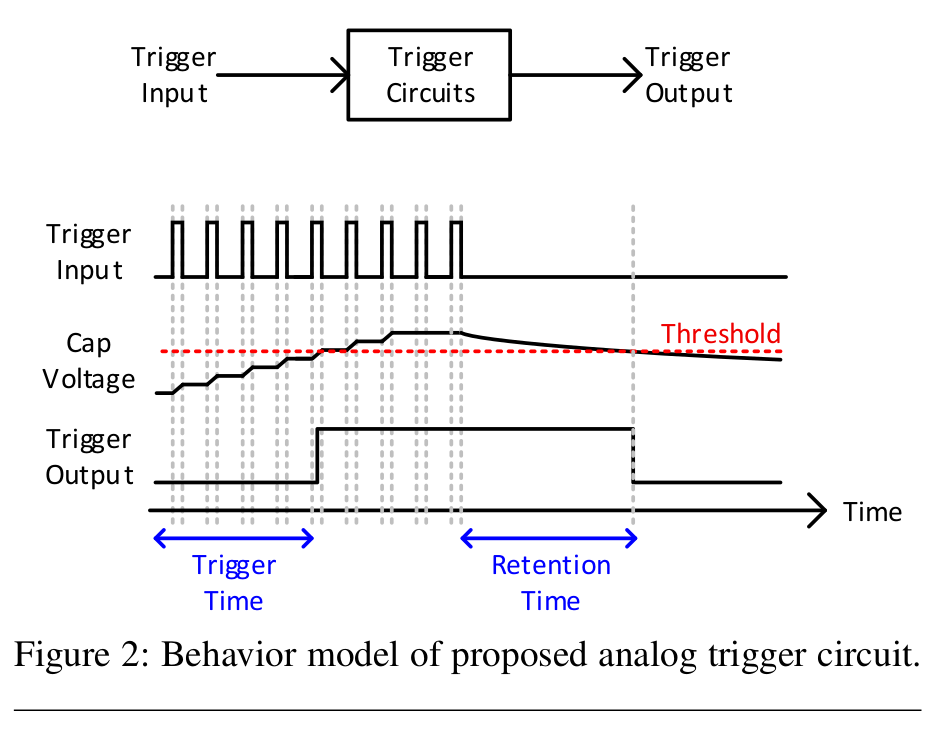
“In the open spaces of an already placed and routed design, we contruct a circuit that use capacitors to siphon charge from nearby wires as they transition between digital values.”
“When the capacitors fully charge, they deploy an attack that forces a victim flip-flop to a desired value, e.g the privileged bit for the processor.”
“We replace the hundreds of gates required by conventional counter-based triggers implemented using digital logic with analog components – a capacitor and a few transistors wrapped-up in a single gate.”
- A2: Analog Malicious Hardware, SP, 2016. ↩
If you could revise
the fundmental principles of
computer system design
to improve security...
... what would you change?