Ruwas Lam
Reference1
A brief summary from ICSE 2006[^ICSE2006]:
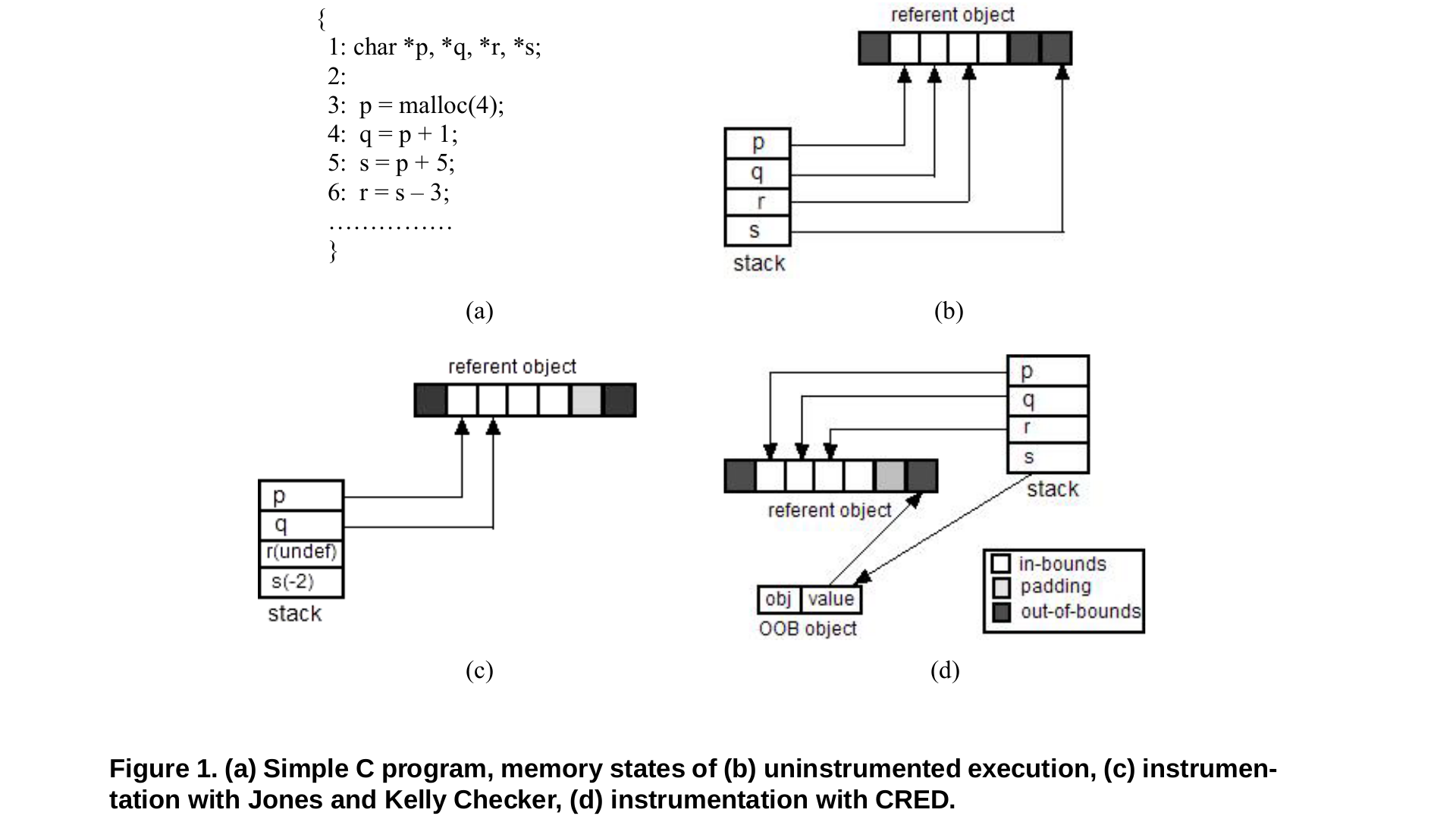
To solve the illegal immediate problem that larger than 1 byte out of bounds, Ruwase and Lam extend the JK algorithm essentially by tracking the intended referent of pointers explicitly but only in the case where a pointer moves out of bounds of its intended referent.
For every out-of-bounds pointer, an extra OOB object is allocated to hold some metadata for the pointer. The pointer itself is modified to point to the OOB object. The OOB contains actual pointer value, and the address of intended object (saved when the pointer first goes out of bounds).
All OOB objects are stored in the hash table. The hash table is checked only before accessing the OOB object to ensure it is a valid OOB object address.
All further arithmetic on the OOB pointer is performed on the value in the OOB object.
If the pointer value comes back within bounds, the original pointer is restored to its current value and the OOB object is deallocated.
- reference ↩
If you could revise
the fundmental principles of
computer system design
to improve security...
... what would you change?