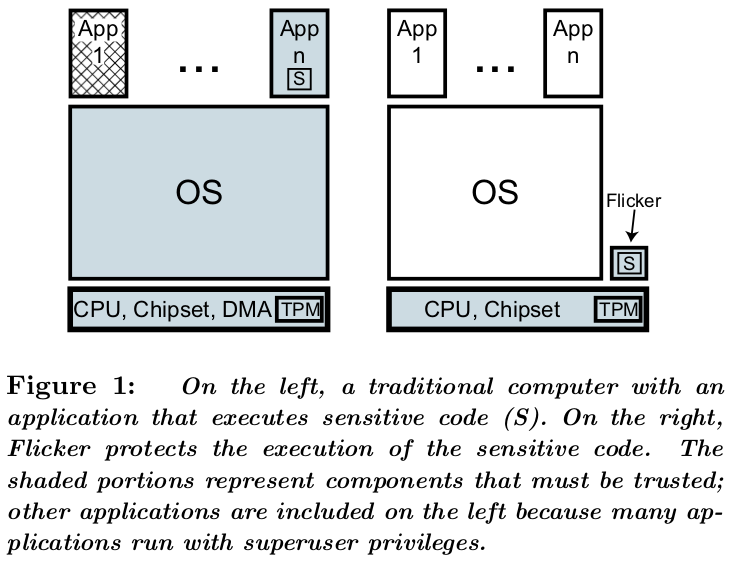
Flicker
Flicker1:
- 250 lines of code trusted;
- No trust on BIOS, OS, DMA devices.
- Trust processor (AMD/Intel)
Fine-grained Attestation:
- e.g. A piece of server code handling the client password; no trust on all other softare stack from BIOS to OS.
- e.g. A Certificate Authority (CA) could sign certificates with its pricate key, even while keeping the key secret from a malicious BIOS/OS/DMA-enabled devices.
Use of Flicker can be attested.
Executed code, its input and output, can be attested.
Processor Features:
- Late launch and attestation
- Flicker: An execution Infrastructure for TCB minimization. EUROSYS, 2008. ↩
If you could revise
the fundmental principles of
computer system design
to improve security...
... what would you change?